tags : VPN, Networking, Security, Anonymity
What
Read these
- Tor Is Not Just for Anonymity
- You’re here because you wanted to use Tor with VPN. Read here.
- index - TOR
- How can we help? | Tor Project | Support
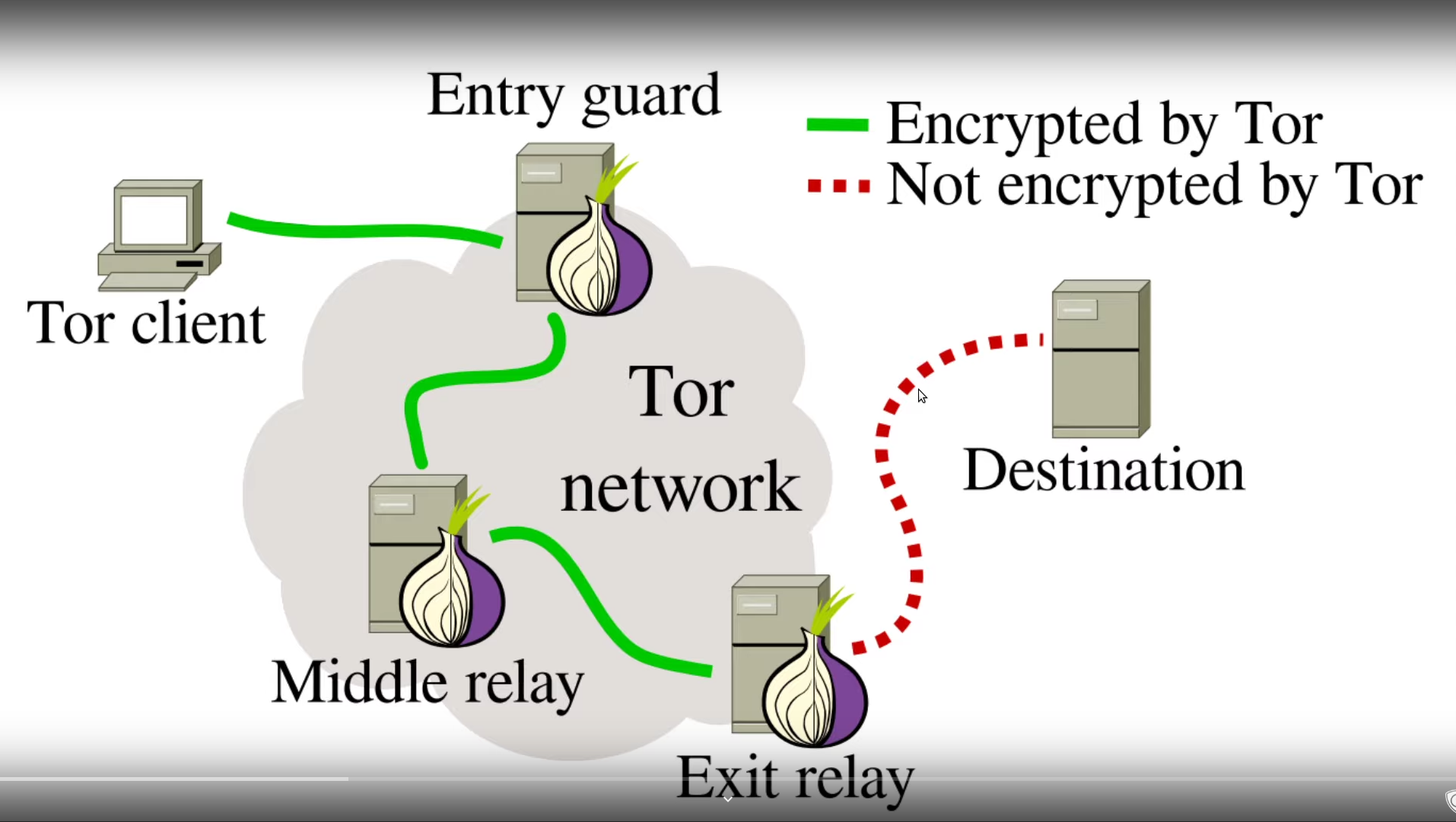
Nodes
Nodes are also refered to as simply relays sometimes.
- Entry-Node (Knows your address and relay nodes address)
- Relay-Node (knows entry-node and exit-node address)
- Exit-Node (knows address of relay-node and webserver)
- Obfuscated nodes/Bridges: These can be used to hide TOR usage, It’s just a node which is not listed in the public list of nodes. This will help making sure you ISP does not realize you’re trying to connect to TOR. See
obfs4. It’s called Bridge because it bridges the clearnet to the TOR network. - Snowflake: It’s a pluggable transport, the whole point is that nobody knows about them. Censors may target the connection between the client and the entry node in an effort to stop the client from connecting to the Tor network.
client --> Snowflake --> Bridge/Entry Node --> Tor network
client --> Bridge/Entry Node --> Tor networkNotes:
- Entry node does not need to know destination address because it’ll just send to random nodes and only the exit node cares about the actual destination
- Entry node can also be a middle node/relay node for someone else.
UDP
- TOR plans to support UDP but it’s not there yet.
- Why it does not support UDP can be found here.
Combining X with Tor
See TorPlusVPN · Wiki · Legacy / Trac · GitLab (Good guide)
Different ways to combine Tor with X have different pros and cons. You can decrease your anonymity by using X w Tor. But IYKWYD you can increase anonymity, security and privacy.
More layers does not necessarily equal more protection. The vast majority of the time.
When you use X, X acts either as a permanent entry or exit node. Because different X work at different levels, they introduce their own challenges when combining them with Tor. Eg. VPN operates on network level, A SSH tunnel can offer a socks5 proxy, HTTP Proxies operate on application level etc.
Using with VPN
There are way too many blogposts on the internet advocating against VPN+TOR. As this post suggests, to mix the two is to essentially mix trust models. That could be considered a sign that one does not understand their own threat model.
But there are certain cases where VPN+TOR makes sense. Consider this:
- Tor
- Gives better anonymity
- Can access onion sites
- VPN
- Can protect UDP traffic (onion doesn’t handle UDP)
- Can protect traffic from ANY app/service, not just Tor Browser
- Is blocked less than onion network
- Has lower performance penalty than onion
Now we see that the two can have different purposes.
- You run VPN 24x7, to protect all of my non-Tor traffic.
- Use Tor Browser to access an onion site, leave VPN running. Tor over VPN.
- The VPN is not there to help Tor, it’s there to protect the non-Tor traffic.
So the whole argument of TOR+VPN holds true that using VPN with TOR will not give you any net gain but it can help you protect other things which are not TOR specific.
Other than that, there are so many tradeoffs. For example:
- Against VPN+TOR: VPN companies are juicer targets for hackers who want to uncover lots of people doing illegal/embarrassing things as compared to some random residential ISP.
- For VPN+TOR: When VPN traffic won’t draw attention but Tor traffic would. But it adds the potential cost of increased identifiability.
So basically this can go back and forth. Consider your situation and see if VPN+TOR makes sense for you. Even if you do make sure it’s TOR over VPN.
TOR over VPN
User->ISP->VPN->Tor : At best a net zero gain for anonymity
VPN over TOR
User->ISP->Tor->VPN : Detrimental to anonymity.TOR over VPN
- VPN is running in background, You open TOR browser.
- VPN doesn’t help or hurt and VPN helps protect all of the non-Tor traffic
VPN over TOR
You can also route VPN connection through TOR. However, you can’t readily do this without using virtual machines. And you’ll need to use TCP mode for the VPNs. This does not make a lot of sense and hard to do and doing so has no point.
Resources
Discussions
Alternatives
Here’s a good list of TOR alternatives(list is more than just alternatives)
I2P for example, is said to handle DDOS attacks better than TOR and is more focused on facilitating hidden services v/s being a clearnet proxy.