tags : WireGuard, TOR, VPN, Proxies, TLS, Networking, Infrastructure
Exposing your home network
Either for personal access or for public access. You want to expose only the absolutely required services to the outside world. That can be achieved by different means and technologies, even redundantly sometimes. This is a world of DNS, VPS , TLS cert management, dyndns, port forwarding, hole punching, etc etc.
For what I know there are 2 ways to expose yourself on the internet: Port Forward and VPN. Details follow.
Port Forwarding
Directly port forward
This is basically opening a port on your router and redirecting it to the required service. This requires a public IP and cannot be done if you’re behind a CGNAT. This is somewhat insecure as it exposes your local network directly into the public network. If you do this make sure to have security in place. Here’s a guide to port forwarding
VPS as Bastion (No VPN)
See this post for an example.
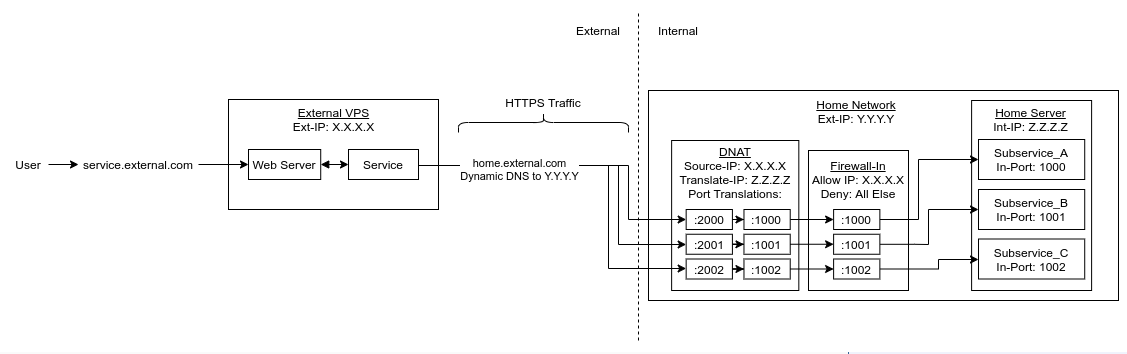
- Web server on VPS for use by external users which interfaces with services in the home network.
- Runs a combination of DNAT+Firewall on home router which only permits access to the internal services from a specific IP (the VPS)
- One could use VPN between VPS and Home network here but it won’t give a lot of benefit in this case other than encrypting the traffic
- This setup also expects a public IP in the Home network. The VPS sort of acts as the bastion and DMZ. One could do the same directly(skipping bastion) in the home-network but again would need to setup the appropriate DMZ.
VPN
Home VPN + DDNS + Public IP
- This is pretty neat and it costs you nothing at all, but assumes you have a public IP assigned to your home network(doesn’t matter if it’s dynamic or static, but needs to be public).
- Once you have a Public IP, you can use DDNS service to solve the problem of changing public IPs.
- Have a VPN server(Wireguard) at home and expose your network through VPN+DDNS. You’ll need to configure WG in a way that end device that connects to your homeserver only connects for access and does not pass all its traffic through your home VPN.
- Tightening
Home VPN + DDNS + CGNAT (Doesn’t work)
- With CGNAT, no incoming connections possible
- DDNS does not work if you don’t have a public IP. The purpose of DDNS is to register your public IP to some name.
- So what can you do?
- Setup a VPS VPN with reverse tunneling to home network or some variant of it.
- Use IPv6
Home VPN + DDNS + IPv6
I am not sure how this will work out but should work out.
VPS VPN
- It boils down to setting up some kind of long-lived connection with a machine with a public IP and setting up a VPN with reverse tunneling to the CGNAT location. Essentially port forwarding/forwarding complete public IP to the home network.
- You can configure VPN client and server to route all traffic from your web server out of the wireguard tunnel through the VPS.
- This will work even if you’re behind a CGNAT
- This essentially puts your VPS on the same local network as your local homelab and you’ll have access to everything
- Check mochman/Bypass_CGNAT for an example topology. They probably call this the Reverse Proxy-over-VPN (RPoVPN) or the Road Warrior Setup.
- Vanilla Wireguard can be used for this.
- Tightening
- Better to have a local reverse proxy and firewall in place if exposing services
- For the VPS, make sure it is set up correctly and hardened sufficiently as this sort of becomes the Bastion.
- A reverse proxy will not secure your proxied services automatically. You’ll need to set some kind of middleware. Can be basic auth, If using cloudflare you can use a single sign-on rule, otherwise check these out
VPS VPN + Mesh
It basically helps to broker a connection between two clients. That’s easy if one or both has a public routable IP. These mesh like VPN(details differ ofc.) solution use their public routable nodes to create the path for the P2P tunnel, no port forwarding required on your end. Occasionally, there is no way to establish a direct p2p path, and the service relays your traffic between nodes.
- This is good for permanent connections between users and services.
- The downsides is that you must have the VPN client on your device in order to connect
- Examples: TailScale, ZeroTier, OpenZiti, innernet, Netmaker, Nebula, Yggdrasil network etc. See full list for WG meshes and other comparisons.
Throwaway tunnels
- anderspitman/awesome-tunneling: List of tunneling software and services. Focus on self-hosting.
- We sort of have a winner here: Cloudflare Tunnel, so rest of this section will be about it.
- Usecase is specific:
- Good for exposing public only services, cloudflare becomes the reverse-proxy and you get all the cloudflare protection.
- Give temp access to your services. Close these tunnels when you’re done.
- Good stuff: Has MFA, DDoS protection, No bandwidth limitation except streaming video(against TOS), Can do without a dedicated reverse-proxy
- Maybe bad stuff: Cloudflare will force using their TLS certificate which means they can decrypt all your traffic. (I have to verify this)
Reverse proxy + SSH
- This can be considered a poor man’s VPN
- A reverse proxy is initiated from your local network outward to your vps. This way, there are no holes in your firewall
- Lets assume you want to expose a website to the outside world
- On the webserver inside your network:
ssh -f -N -R 0.0.0.0:80:0.0.0.0:80 root@addressofvps - That’s it. SSH will connect to the VPS, and listen on the VPS side on port 80, then forward it to your webservers port 80
Selfhosting Lingo
There are few pointy things to be aware of when making decisions about vendors, how to do things, what to buy etc. Few terms or set of terms that I think I might want to keep a note of.
Egress/Ingress
Suppose you’re running a VPN in a server and they charge you only for
egress
- Ingress
- Traffic coming into your VM. For example, if over your VPN to request a website in your browser, this request from your browser to the website would be ingress to the VM.
- Egress
- Traffic leaving your VM. Using the above example, traffic that leaves your VM to the website to get the request is egress. When the VM get’s the response from the website (ingress, free), it then has to send that response over the VM to your computer (egress, not free).
- Cloud companies charge egress fees when customers want to move their data out of the provider’s platform. i.e more egress fee = sort of vendor lock in attempt
Visually, a request/response to a website over your VPN looks like this:
Your PC ----ingress---> VM ----egress---> Website
Website ----ingress---> VM ----egress---> Your PCIn this case, you are charged for all egress.
local/onsite/offsite backups
- Local: copy in your machine
- Onsite: External drive fits perfectly
- Offsite: Either cloud storage or an external drive that you can keep in a different location.
sync/backup
- Backup tools would be able to do versioned backups, would store them in their own extension, possibility of incremental backups and much more else.
- Syncing data will store the data in the same file extension as original data, also won’t protect you from accidential deletion and etc.
Understanding this helped me better plan my backup strategy.
- Sync
- When you’re using a sync service, you can easily delete or change a file, save it, and then lose the one you actually wanted to keep.
- Allow you to access your files across different devices.
- Share files with other users
- Backup
- Usually work automatically in the background of your computer
- Backing up a copy of your new or changed data to another location
- A good backup will have versioning and restore set correctly
Flat tired/Tired pricing
- Flat tired Pricing: Charges the user based on the storage volume, and cost is typically expressed per gigabyte stored. There is only one tier.
- Tired Pricing: A provider may have a small business pricing tier and an enterprise tier.
Minimum Retention Periods
It sounds innocent but some providers may charge you for deleting data before the retention period! beware.
Resources
Media Server
FAQ
SMB vs NFS
SMB, more properly known as CIFS, is a very chatty TCP only protocol for file and printer sharing, that includes some security (passwords, encryption, etc). NFS is a much more efficient protocol just for files, and can run over TCP or UDP (depending on version), and historically didn’t offer much in the way of security. Newer versions can use kerberos & some other mechanisms, but traditionally who can access the files is based on IP address only.
- SMB better supported in windows
- Windows by default does not have a NFS client
Reverse Proxy and Auth
- Identity Providers(IDP): Keycloak, Authentik, Authelia
- If service has its own user management
- No reason to put
Identity Providerin front of it. Just don’tforwardAuthon traefik router. - See if you can use LDAP to serve as a single source of truth for users.
- No reason to put
- If service has its own user management + support OIDC(OpenID Connect)
- use
Identity Provideras an OIDC provider. (this will help with SSO)
- use
- If service has no user management
- use
forwardAuth+Identity Provider.
- use