tags : SSH, GPG, Security, Networking, Cryptography
What
Basics
- X.509 ( See X-Standards) PKI enables each certificate to be signed by a single party: a certificate authority (CA).
- It allows severs to be authenticated without requiring clients to manually install root certificates.
- Bestows trust throughout the hierarchy of certificates which lead back to them.
- One alternative to PKI is Web of Trust which GNUPG uses
Main Components
- Certificate Authorities (CAs) (See TLS)
- Registration Authorities
- Digital certificates
- Public and private keys
- Certificate revocation lists
Key protocols
PKI does not necessarily mean asymmetric key encryption. For example, DH is used for PKI but it aims to create a symmetric key in the end. See this and this answer for more details.
Diffie hellman
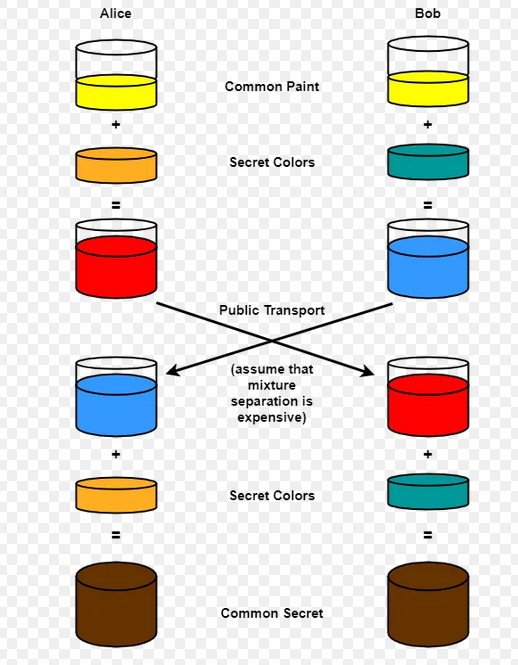
- Relies on the hardness of taking logarithms (discrete logs)
- DH uses a multiplicative group of integers modulo a prime p
RSA
- Relies on the hardness of factoring.
DSA (Digital Signature Algorithm)
- It weak, can be broken?
Elliptic curve (ECC)
Key exchange method
- The key exchange yields the secret key which will be used to encrypt data for that session.
- SSH uses DH to establish an ephemeral (ie: one time) key to establish forward-security.
-
ECDH
- Variant of DH that uses a multiplicative group of points on an elliptic curve
- Uses a curve
- NIST curve P-256
- Curve25519/cv25519/X25519
Signature schemes
- SSH uses RSA/ECC variants to establish an initial secure, authenticated connection
- The signature is so that the client can make sure that it talks to the right server
-
ECDSA
- NIST produced, political concerns
- Can be susceptible to attacks. Underlying DSA.
- Just use Ed25519 instead
-
Ed25519
- Strongest so far
Resources
- Ed25519 Keys | Brian Warner
- cv25519 vs ed25519
- Introducing Elliptic Curves – Math ∩ Programming
- Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?
- A (relatively easy to understand) primer on elliptic curve cryptography
- EdDSA, Ed25519, Ed25519-IETF, Ed25519ph, Ed25519ctx, HashEdDSA, PureEdDSA, WTF?
Keys
Public key
- Public key can be derived from the private key
- They are meant to be public, fr. No point trying to keep it secret.
- The design does not guarantee that the public key cannot be derived from the encrypted material.
Private key
- The design guarantee that the private key cannot be derived from the encrypted material.
Encrypting
See Encryption
Signing
- ORDERING MATTERS. Do due diligence. See this
- It’s suggested that we do
sign-then-encrypt - Because with
encrypt-then-signthe sender might be unaware of the actual content of the message.
- It’s suggested that we do
- When X wants to send you an encrypted message, they’ll use your
public key. - So now you got a package that you think came from X.
- You open it, it’s encrypted.
- You decrypt it, it gets decrypted. Nice.
- But now you have no idea, if that package was tampered or MITM’ed or something, because anyone with access to the
public keycan easily create a file that will pass any file modification tests - This is why we need signing
- When signing, X can sign the message with their
private key.- Now if you want to verify if it was
Xthat sent the message - You use
X’spublic keyto verify that the message certainly came fromX - And ofc then use your own
private keyto decrypt rest of the message for yourself.
- Now if you want to verify if it was