tags : Operating Systems, Orchestrators and Scheduling, QEMU, Containers
Intro
- Virtualization: creating and running virtual machines
- It is handled by something called a hypervisor
- Hypervisor can either be:
- software
- firmware
- hardware
Types
Type 1
AKA True virtualization
- Run on bare metal and typically leverage features of the CPU specifically built for virtualization. Eg. AMD-V and Intel VT-x.
- Can only emulate the same architecture as of the host CPU
- Examples
- KVM/Proxmox (Not exactly)
- VMWare ESXi.
- Microsoft Hyper-V
Type 2
AKA Emulation
- Run on top of a host OS, and thus it translates system calls made by the guest OS to system calls made to the host OS.
- Can emulate any and all architectures regardless of the host CPU, at least in theory.
- Examples
- QEMU. (Not exactly) See QEMU
- VMWare Workstation.
- VirtualBox.
Case about QEMU+KVM
- QEMU uses KVM
- QEMU and KVM are neither type 1 nor type 2; somewhere in between.
- If KVM Module
- Present: QEMU will leverage KVM and act halfway between type1&2.
- Absent: QEMU will provide emulation rather than virtualisation.
- About KVM itself, it’s not strictly a type-1 hypervisor, as it still is part of an OS,
Ecosystem
Libvirt
Libvirt is an open-source set of api, daemon, cli and libraries which provide a single way to manage multiple different hypervisors It can handle QEMU, KVM, Xen, LXC, OpenVZ, VMWare ESXi, etc.
Some Notes
- VMWare offers graphics acceleration for Windows guests that seems to be unmatched in KVM (without using PCIe passthrough).
- VirtualBox has a basic 3D acceleration support for Windows guests that KVM/QEMU still doesn’t have without GPU passthrough.
Others
CPU Pinning
It moves processes from the host away from certain CPU cores, while devoting the guest entirely to these cores. This way, the ‘pinned’ CPU cores are dedicated to the VM,
Virtual Machines (The ISA one)
In fact, x86 seemed to be doomed at the turn of the century. Much was made of perceived performance boundaries of the x86 ISA; the most common prediction being a shift to “very large instruction word” (“VLIW”) architectures. There was a scramble to find a way to build a compatibility bridge from x86 to this VLIW future.
The 1997 DAISY paper, 1998’s “Achieving high performance via co-designed virtual machines”, and 2003’s “LLVA: A Low-level Virtual Instruction Set Architecture” originated the idea of a “virtual instruction set architecture” (“virtual ISA” or “V-ISA”) to address the inflexibility and seemingly imminent obsolescence of x86. They were written in reaction to Java’s virtual machine; the LLVA paper in particular defines several useful design goals for both the “Virtual Instruction Set Computer” (“VISC"") and “Virtual Abstract Binary Interface” (“V-ABI”) in order to differentiate their approach from the JVM.
Isolation and Sandboxing
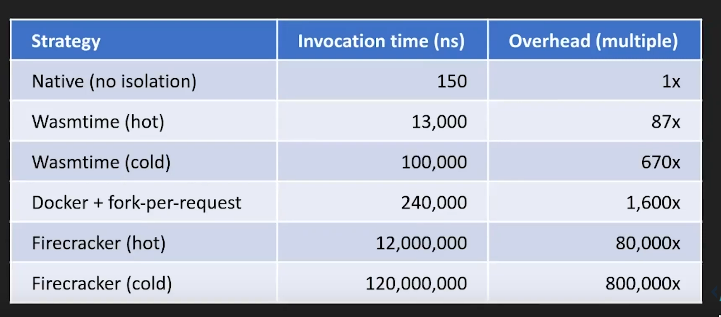
Remote code execution/ Sandboxing (Untrusted)
At the moment, this can be one of 2 ways largely
WebAssembly
See WebAssembly
- JS Interpreter
- Python Interepreter
- Others
- Adding Python WASI support to Wasm Language Runtimes
- https://github.com/taybenlor/runno
- In-browser code playgrounds
- Runno WASI
- Sandboxing LLM Generated Code with Extism
- Universal Code Execution by Chaining Messages in Browser Extensions | Hacker News
- Show HN: Execute JavaScript in a WebAssembly QuickJS sandbox | Hacker News
VM
Browser sandbox
Resources
- Ask HN: Pros and cons of V8 isolates? | Hacker News
- https://e2b.dev/
- Landrun: Sandbox any Linux process using Landlock, no root or containers | Hacker News
- TinyKVM: Fast sandbox that runs on top of Varnish | Hacker News
Resource
- Virtualization and Hypervisors
- Why We Replaced Firecracker with QEMU | Hocus Blog (See HN discussions aswel)
- Solving the 100GB Game Download | Hacker News
- Understanding QEMU devices - QEMU
TODO Image Types
ISO
.img
qcow
MicroVM
Firecracker
- Building a Firecracker-Powered Course Platform to Learn Docker and Kubernetes | Hacker News
- Grab your lab coat - we’re building a microVM from a container
- A brief history of our serverless future – Jonathon Belotti [thundergolfer]
- AWS Lambda turns 10: A rare look at the doc that started it | All Things Distributed