tags : Linux, Networking, Security
Kernel packet filters
These are kernel specific
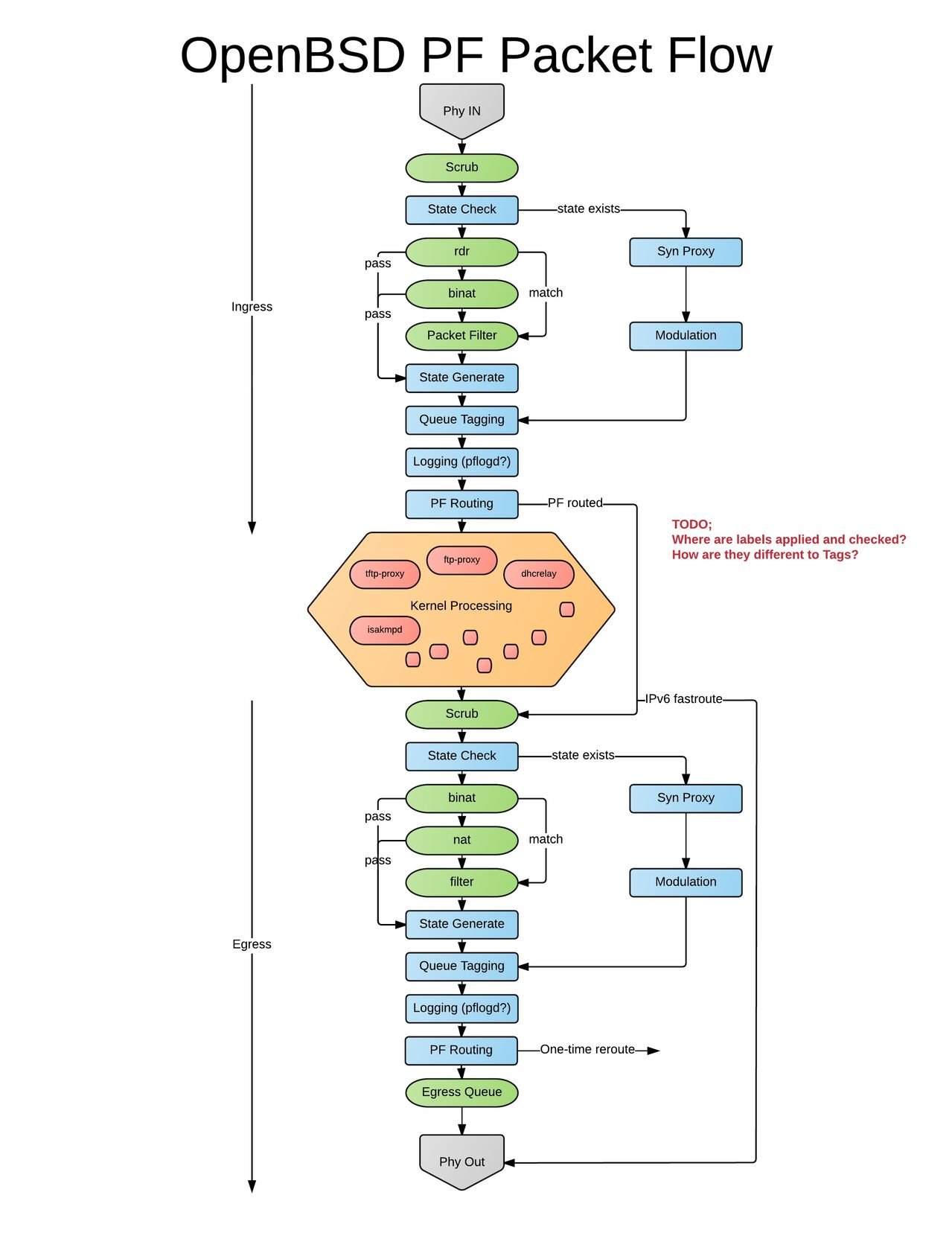
OpenBSD
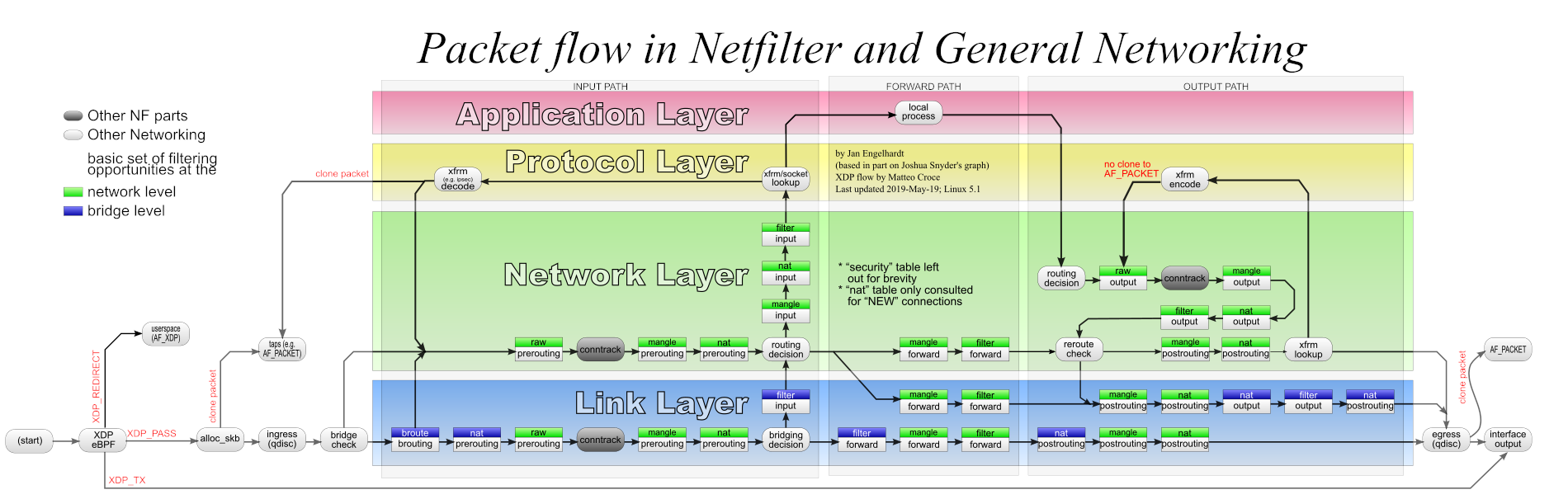
Linux
- Userland APIs/Frontends to netfilter: iptables, nft, iptables-nft, conntrack etc.
- Configuration managers: Firewalld, ufw, opensnitch etc.
Linux firewalls
History: ipchains -> iptables -> nftables / iptables-nft -> bpf(?)
iptables
- See iptables for more info.
- It’s just a frontend to netfilter that deals with certain things. (Eg.
tccontrols another portion of netfilter) - It’s more than a userland tool. It’s a set of tools for different protocols. (Sometimes called
Xtables) Different kernel modules and programs are currently used for different protocolsiptablesapplies to IPv4ip6tablesto IPv6arptablesto ARPebtablesto Ethernet frames
iptablesis deprecated, long liveiptables-nft. Theiptables-nftcommand uses the newernftableskernel API but reuses the legacy packet-matching code.
λ readlink -f $(which iptables)
/usr/bin/xtables-nft-multi
λ iptables -V
iptables v1.8.7 (nf_tables)nftables (nft)
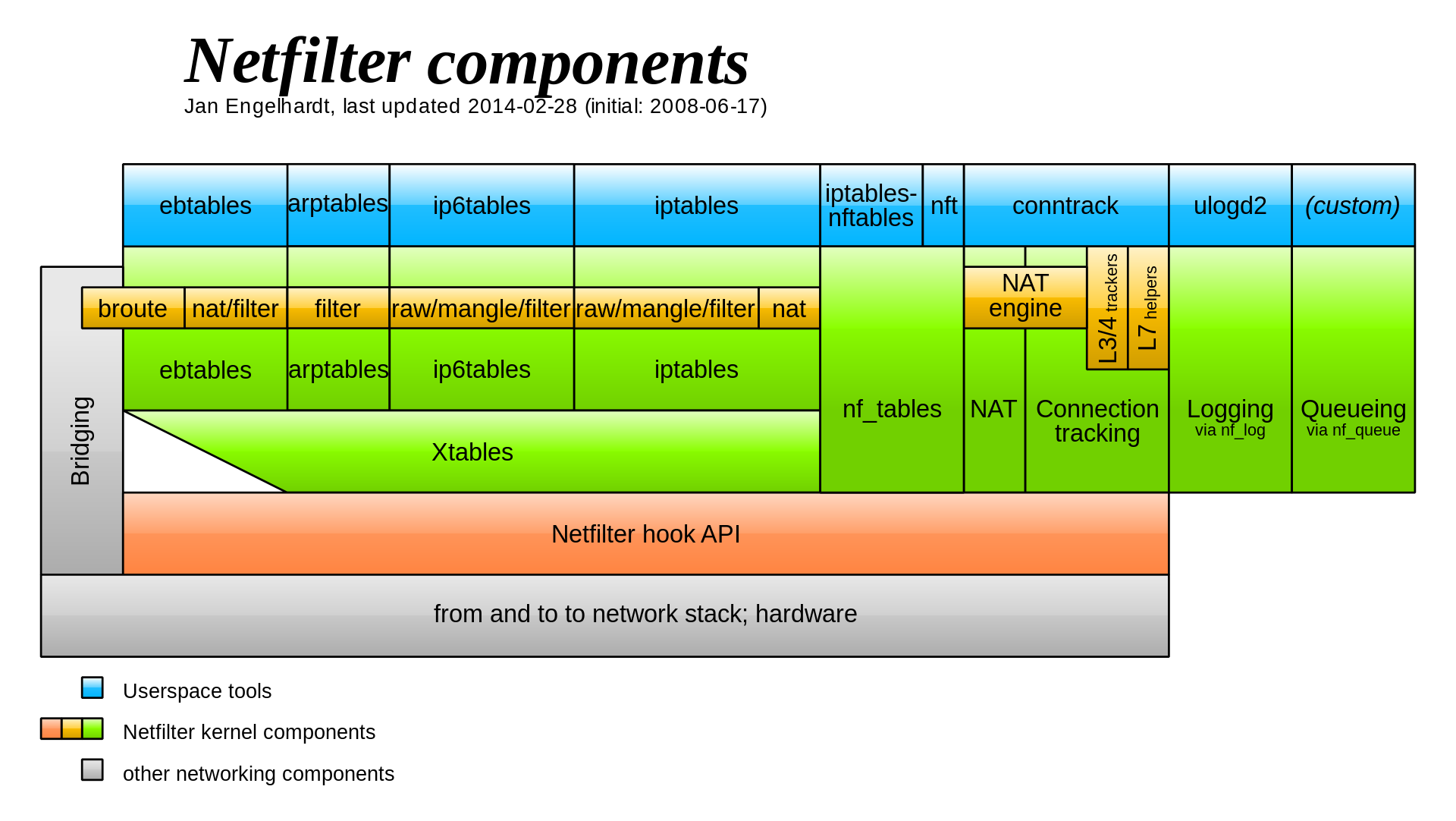
- iptables, ip6tables, arptables, ebtables simplified to just nftables.
- nftables is what is implemented in current systems/kernels, they have glue/translation versions of iptables (
iptables-nft) that internally write nftables rules into the system.
BPF what?
⚠ I am not sure about this one. I asked a question in the cilium slack about this blogpost about BPF replacing existing firewall vs these newer posts pointing otherwise but I got no response.
According to internet news, nftable is already deprecated in the future by Linux Kernel. The future will most likely be BPFilter, which is based on eBPF, but that is still several years out. They have to build the generic BPF/XDP system before they could build a full iptables/nftables/netfilter (maybe) replacement on top. Companies like Cilium, Facebook, and Cloudflare from jumping ahead and doing firewalling with the BPF parts that are already there.
Learning path
- Learn iptables syntax first with
iptables-nft(Lot of good learning materials) - Learn nftables, then maybe try out the config managers like firewalld.
- See BPF / XDP if interested.
- Using iptables-nft: a hybrid Linux firewall
ipset?
- Initially, standard practice of ACLs implemented by iptables was to use sequential list of rules
- i.e. every packet Rx or Tx is matched against a list of rules, one by one.
- As time passed and iptables grew, traversing sequential iptables lists had become unbearable from a performance and latency perspective.
- Issue: Long lists of rules either rejecting or allowing individual IP address and port combinations
- Workaround: ipset, allows compressing list of rules matching on IP/port combinations into hash table reducing no. of rules.