tags : Linux
Flow
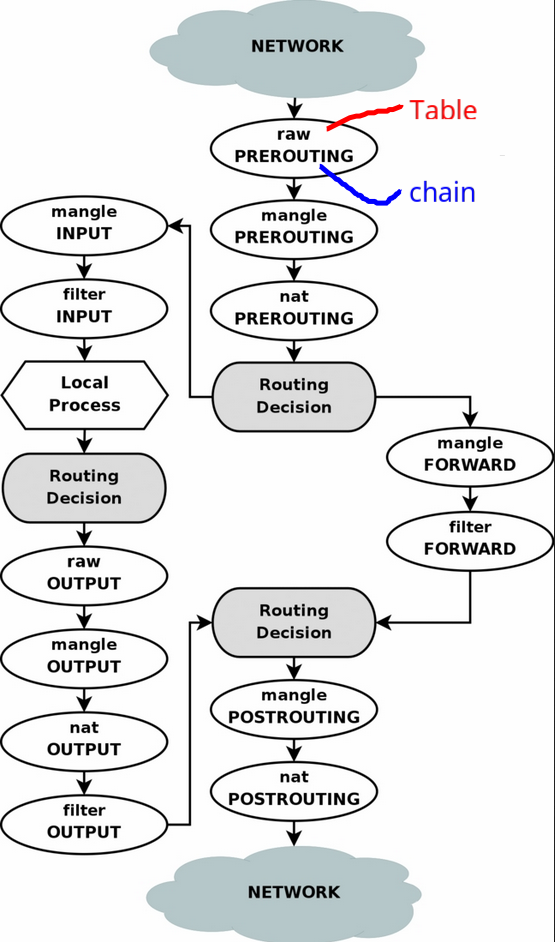 See this for explanation.
See this for explanation.
Packet
- All interfaces are handled the same way
- Every IP packet that comes in on any network interface passes through this^ flow chart from top to bottom.
- Internal interfaces are handled the same way internet facing interfaces are handled.
Tables(5)
tables contain chains of rules for how to treat network traffic packets. Following are tables ordered by normal user usage frequency.
- filter: Control the flow of packets in and out of a system. Default table. Firewall related.
- nat: Redirect connections to other interfaces on the network and natting, port forwarding etc.
- mangle: Modify packet headers/specialized packet alterations.
- raw: Only for configuring packets so that they are exempt from connection tracking.
- security: Mandatory Access Control networking rules (e.g. SELinux usage).
Chains
Lists of rules which are followed in order. Chains can be builtin or user defined.
Eg. Chain1 = [rule1, rule2, rule3, rule4]
Chains are per tables. That means, the chain OUTPUT on the nat table is different from the chain OUTPUT on the filter table.
- Only built in chains have a default policy. Generally set to
ACCEPT, can be changed toDROP.- Packet has to pass through all existing rules in chain before the default policy is applied.
:some_user_def_chain - [0:0]: Default policy will be-with a custom chain.
Basic idea of chains
Built-in chains represent the netfilter hooks which trigger them.
PREROUTINGNF_IP_PRE_ROUTINGhook
INPUT- Protect local applications from receiving unwanted network traffic
NF_IP_LOCAL_INhook
FORWARD: Filter network traffic forwarded/routed by the linux system or between network interfacesNF_IP_FORWARDhook
OUTPUT- Protect local applications sending undesired network traffic. The destination is usually another host, but can be the same host via the loopback interface.
NF_IP_LOCAL_OUThook
POSTROUTINGNF_IP_POST_ROUTINGhook
Built in chains
- filter:
INPUT,OUTPUT,FORWARD - nat:
PREROUTING,INPUT,OUTPUT,POSTROUTING - mangle:
INPUT,OUTPUT,PREROUTING,POSTROUTING,FORWARD - raw:
PREROUTING,OUTPUT - security:
INPUT,OUTPUT,FORWARD
Traversing Chain
- 1st routing decision: Decide if the final destination of is the local machine (
INPUTchains) or elsewhere (FORWARDchains). - Subsequent routing decisions: Decide what interface to assign to an outgoing packet.
- Chain -> Rule(Evaluate)
- If Match: Execute target/jump action
- If target
DROP: Packet is dropped and no further processing is done. - If target
ACCEPT: No traverse any further rules/chain of the table. Processing will jump to the first chain of the next table in order.
- If target
- If No Match: Packet is dropped back into the calling chain
- If Match: Execute target/jump action
Rules
Rule refers to an action to be configured within a chain.
Rule = Match(s) + Target/Action
Matches
Match is something that specifies a special condition within the packet that must be true (or false)
Generic matches
A generic match is a kind of match that is always available, whatever kind of protocol we are working on, or whatever match extensions we have loaded.
--protocol/-p--source/-s--destination/-d--in-interface/-i--out-interface/-o--fragment/-f- Match the second and third part of a fragmented packet.
- With fragmented packets, there is no way to tell the source or destination ports of the fragments
Implicit matches
Implicit matches are implied, taken for granted, automatic. These are protocol specific.
- TCP :
--source-port,--destination-port,--tcp-flags,--syn,--tcp-option - UDP:
--source-port,--destination-port - ICMP:
--icmp-type - STCP:
--source-port,--destination-port,--chunk-types
Explicit matches
Explicit matches are those that have to be specifically loaded with the -m or --match option. See man iptables-extensions for these. (Eg.conntrack module)
Targets
- All targets are not valid in all tables
- Specified by
-j/--jump - Targets are either terminating (as built-in targets) or non-terminating (as user-defined chains). Target exts. can be any.
- Can be
- User defined
chain - Builtin targets(
ACCEPT,DROP,QUEUE,RETURN) - Target extensions(
REJECT,LOG, many more seeman iptables-extensions).
- User defined
NAT
NAT allows a host or several hosts to share the same IP address in a way. The NAT server receives the packet, rewrites the source and/or destination address and then recalculates the checksum of the packet. NAT depends on connection tracking.
SNAT (Source NAT)
To forward packets with source IP address X to some network that does not know how to reach X or would try to reach X the using the “wrong” route.
- For the local network use one of the private IP ranges
- SNAT will then turn all local private addresses into it’s own public IP
SNATandMASQUERADEare almost the same- With
SNATtarget, we only have static ip assignment. - With
MASQUERADE, it will automatically set the new source IP to the default IP address of the outgoing network interface. Useful for DHCP stuff. (This is what is used in most modern setups) - The kernel internally keeps track of the outgoing packets and their original source addresses, and when the response packets are received, it replaces the destination IP address with the appropriate private IP address.
- With
- The
MASQUERADEtarget is only valid in thePOSTROUTINGchain of thenattable. - Original source address differs from the reply destination.
DNAT (Destination NAT)
Have a private server be available publicly by specifying a local destination IP:PORT where incoming packets requesting to access internal service can be forwarded to.
- Usually happens in the
PREROUTINGchain of thenattable - Original destination differs from the reply source.
- TODO: I think DNAT happens in combination of
natandfiltertable????