tags : HTTP, Networking, Subnetting, Load Balancers, Web Performance, Network Programming
The case of 0.0.0.0 & Localhost
What about 127.0.0.1
127.0.0.1 is normally the IP address assigned to the “loopback” or local-only interface.
Multiple meanings of 0.0.0.0
Meaning of 0.0.0.0 is contextual.
non-routable meta-address used to designate an invalid, unknown, or non-applicable target
- Route entry
- Usually means the default route.
- Webserver
- 0.0.0.0 means all IPv4 addresses on the local machine.
- Listen on every available network interface
- This explicitly limits the listening daemon to IPv4 for no good reason.
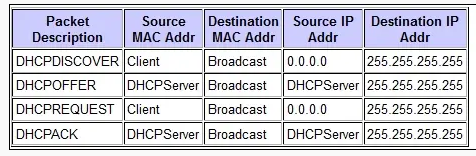
- DHCP
Used as source IP by clients during DHCP.
FAQ
Sockets and Connections
- A connection (See HTTP) does not occupy a
port. - The only hard limit for connections the number of open file descriptors on the server. But performance can degrade by CPU bound/ io bound operations.
- Every connection creates a new
socket. Some operating systems let you load balance incoming connections between multiple sockets.
How does a web sever handle incoming requests?
- A webserver usually has 1 listening socket.
- But “accepting” the connection duplicates that socket and sets the remote IP and port on the copy.
- So in most cases, no. of connections = no. of active sockets
- I am not sure how it works in the case of UDP.
Resources
TODO Writing a fast server
- https://x.com/hnasr/status/1863784690085449984
- How many concurrent TCP connections
- The C10K problem
- The Secret to 10 Million Concurrent Connections -The Kernel is the Problem
- fast-servers
- Fast UNIX Servers - dankwiki, the wiki of nick black
- djabberd: c10k? hah! - brad’s life — LiveJournal
- Advanced Napkin Math: Estimating Systems
- https://github.com/sirupsen/napkin-math
- Simon Eskildsen - Sirupsen
- Increase HTTP Performance by Fitting In the Initial TCP Slow Start Window
- How much memory do you need to run 1M concurrent tasks? | Hacker News
Notes on Caddy
Local development
What domain to use? .local, .internal, .custom?
- Most systems don’t resolve
*.localto your localhost. But*.localhostdoes usually work in browsers (they directly map those*.localhostdomains tolocalhost, and don’t try to use DNS to resolve them). - So in summary, go with
x.localhost, this means we avoid having to do any/etc/hostsor DNS resolution stuff.
-
Using custom domain for local dev
ALTERNATIVELY, you could use your actual domain for local development
-
this is useful if you want to same-site cookies etc, where your other 3rd party service is hosted in an actual subdomain(eg. r2 bucket etc)
-
Eg.
- set an
Arecord forapp.mylocal.foo.orgto 127.0.0.1 - set an
Arecord forapi.mylocal.foo.orgto 127.0.0.1
- set an
-
In your local machine have caddy be running on
port:80and add thatapp.mylocal.foo.orgto handle the reverse proxy. -
You’ll generate the TLS certs like:
mkcert "foo.org" "*.foo.org" "*.local.foo.org"- NOTE: Second level wildcards are NOT supported by browsers
-
You should be done
-
How will that domain get mapped, manually edit /etc/hosts?
How will the tls certs get provisioned for those?
- You can use the
tls internal
Internal services
You can use the denied directive
# I use some services (like Vaultwarden) only on my LAN-Net, or if I'm "on the way" using VPN. So I configured my Caddy-Instance like this:
# That ensures that it is simply not possible to connect my Server through WAN, even if I expose my Caddy-Server to the Internet.
myvaultwarden.mydomain.com {
@denied not remote_ip private_ranges
abort @denied
reverse_proxy 192.168.1.100:80
}But you could also simply run another instance of caddy in an internal interface(the way i do it, in the tailscale interface)