tags : Web Security, Web Authentication, Security, Javascript, Cookies
Links
- Cross Site Scripting Prevention - OWASP Cheat Sheet Series
- XSS Filter Evasion - OWASP Cheat Sheet Series
Attack types
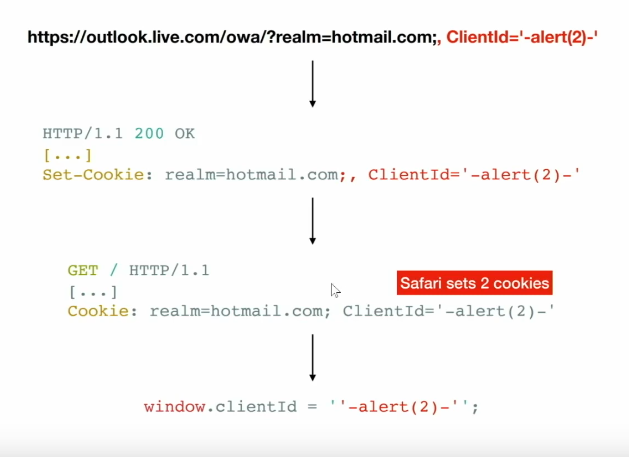
Reflected
- text/code from URL -> Into DOM
- Attacker manually shares the URL
Stored
- text/code from a legit database -> Into DOM
- Eg. If you manage to inject stuff into a forum DB, when the stuff gets loaded for ppl it’ll naively load it for all users and then automatically execute your code.
- So validate everything from “link your social media profile url etc”
DOM based
- Similar to reflected but input comes from 3rd party API
- So hack the 3rd party API and you’re good to go
Prevention
Escape inputs
- Escape inputs from 3rd party sources
- Escape user inputs
CSP
Allow images from anywhere, audio/video from media1.com and any subdomains from media2.com, and scripts from userscripts.example.com
Content-Security-Policy: default-src 'self'; img-src *; media-src media1.com *.media2.com; script-src userscripts.example.com- See https://content-security-policy.com/
- CSP is a way to detect and mitigate XSS, reduce attack surface
- CSP is not a strong security protection, it’s more of a best effort thing
Why CSP?
- Same Origin Policy (SOP) prevents you from reading cross-origin
- CSP is a even stricter policy and highly granular in which you can whitelist specific things only.