tags : Security, Cryptography, Identity Management
What are the broad categories (3)
- Inter Service Authentication and Authorization
- These use things like Kerberos or mTLS (See TLS)
- See Latacora - A Child’s Garden of Inter-Service Authentication Schemes🌟 (https://archive.is/20210227215241/https://latacora.micro.blog/a-childs-garden/)
- Federated authentication and single sign-on
- End user/Retail
- See API Design
More on End user/Retail IAM
- See API Tokens: A Tedious Survey · The Fly Blog
- So here, the winners are sort of
Random Tokensand OAuth (Open Authorization)
Random Tokens
binascii.hexlify(os.urandom(16))- Store random token against each user & associate those users with allowed actions.
- DB hits
Platform Tokens
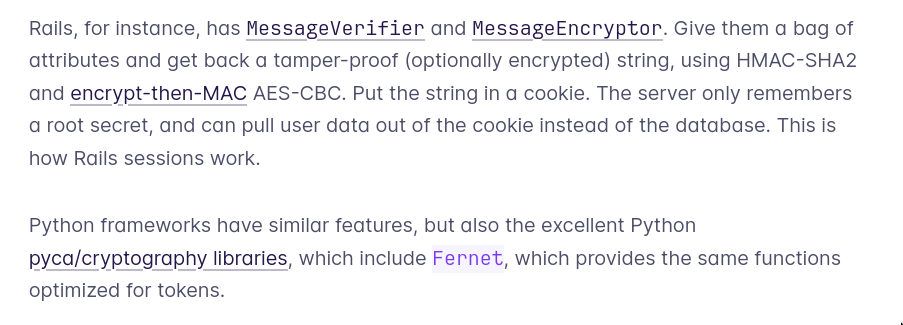
- Use API tokens just the way as Web Session tokens
- No DB hit, API token is basically the encrypted version of user data
- When we get the API token, the backend decrypts it and goes forward etc.
- Suffers from “how do we revoke now?”, solution is usually to version the user in user table, to revoke we bump the version and the version string becomes part of the token. Will suffer DB hits but cache can help
Authenticated Requests
- These are different from HTTP Bearer tokens
- AWS API uses this
- I am not super sure how this works
Oauth2
- OAuth (Open Authorization) is abused as a way of protecting your API but still widely used.
- Tries to think of the issues IAM faces and tries to give solutions to those
- Specs for refresh tokens, Access token(opaque) etc.
- Easy to revoke
- Less DB hits
- Use the
Authorization Code grantif there is a human being involved. - Use the
Client Credentials grantif you are performing server to server communication. - Benefits of using OAuth in APIs
- Time limited (rotation built in).
- If using signed tokens, integrity of contents can be verified.
- Lots of libraries and knowledge around how to use it.
- Tokens allow for more interesting/useful payloads than an API key.
- OAuth (Open Authorization) access tokens are a subcategory of tokens
- Best practices for REST API security: Authentication and authorization
- The complete guide to protecting your APIs with OAuth2 (part 1)
JWT
See JWT
PASETO
Hip JWT
- v1: NIST-compliant AES-CTR, HMAC-SHA2, and RSA
- v2: XChaPoly and Ed25519
- v3: replaces RSA with a P-384 ECDSA
- v4: replaces XChaPoly with XChaCha and a Blake2 KMAC.